Secure Access Service Edge (SASE) is a strong trend emerging in enterprise network security, representing the long-term capability to integrate and consolidate a variety of networking and cybersecurity tools. Let’s do a quick dive on the technology to understand why it’s necessary.
SASE emerged as an outgrowth of the software-defined wide-area networking (SD-WAN) technology movement, which made it easier to configure, orchestrate, and manage WAN connectivity from enterprise branches. One of the key accomplishments of SD-WAN was to push the focus on networks toward software control and applications visibility, which makes it easier for network operators to manage the security and access to cloud applications.
When it comes down to it, SASE is about building more visibility, analytics, and automation into the network. Just as SD-WAN was used in network analysis to distinguish among cloud applications to allow policy-based networking and access, SASE takes this a step further to tie in integration with cybersecurity functions.
SASE is About Integration
If one were forced to underline one key driver to SASE – it’s about integration. Security and network managers are overwhelmed with the number of management tools and security applications need to perform their jobs, and they are looking to consolidate these activities
In our survey work and interviews with end users, the primary driver of SASE is to provide a more unified platform for observing and security networking traffic and applications activity.
In the example below, we asked survey respondents (director-level and above managers in IT security and networking) if they believe the use of SASE technology will grow as part of their organization’s strategy to implement a more agile, pervasive cybersecurity strategy, 85% responded “Yes.” Only 7% said “No,” and 8% said they didn’t know, with a total of 117 responses.
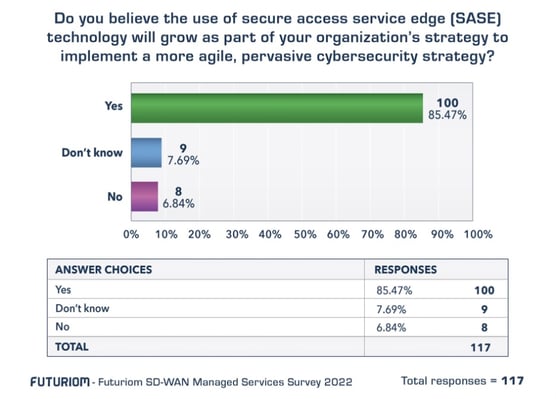
This survey data confirms other data and information we have tracked, including our interviews with practitioners, who often rank the need for better security integration high on their list of priorities.
The specifics of this integration will come down to discrete network security functions and the basket of acronyms used to describe them. SASE represents a consolidation and integration of many different cybersecurity and network functions. Here is a list of some of the acronyms you are likely to encounter in today’s cybersecurity and SASE market:
- Advanced threat protection (ATP)
- Cloud access security broker (CASB)
- Data loss prevention (DLP)
- Firewall-as-a-service (FWaaS)
- Intrusion detection system/intrusion prevention system (IDS/IPS)
- Next-generation firewall (NGFW)
- Software-defined wide-area networking (SD-WAN)
- Secure web gateway (SWG)
- Unified threat management (UTM)
- Zero trust network access (ZTNA)
SASE platforms can be used to add, and orchestrate, these functions along with network connectivity. The integration of these functions is the overwhelming force driving the SASE market.
Network Visibility and SASE Use Cases
Going back to SASE’s origins in SD-WAN, it was about software-based policy control and applications visibility. Because many of the security functions above require the same key elements – deeper understanding and visibility into the network traffic – it makes sense that SASE can serve to consolidate and integrate these functions.
Another way to think of SASE is as a best-of-breed approach to networking and security that addresses many different access scenarios. As the requirements for both cybersecurity and networking increase in a cloud-based world, use cases for SASE are expanding as well.
Here are some of the new use cases and targeted by SASE solutions:
- Compliance. The complexity and diversity of network connections in our cloud-based world demand more visibility and need for security compliance. Using SASE, security policies can be tailored to geographies, specific industry regulations, and generalized privacy needs, such as data disclosure restrictions and anonymization.
- Security for edge Internet of Things (IoT) applications. SASE is an important component of enabling organizations to fully embrace network transformation. Increasingly, SASE engagements will be driven by adoption of 5G and IoT.
- ZTNA/software-defined perimeter (SDP) adoption. ZTNA/SDP products and services reduce the attack surface of assets by limiting access to and visibility of resources. For example, ZTNA/SDP solutions provide application-level, instead of network-level, connections to applications, and by using a trust broker they can eliminate the need to expose applications to potential hackers with direct Internet connections.
- Hybrid workforce access. As workforces become more distributed, VPN augmentation or replacement can provide better scalability, management, and security for hybrid or remote work.
As you can see, many of these use cases have similar threads running through them: Network and applications visibility and control – to help managers set and define policy.
Some SASE Takeaways
SASE represents a reflection of the need for network operators to gain more control over network applications and traffic, including automating zero-trust access, application access policy, and cloud security.
However, SASE is not a panacea for everything. Although some SASE vendors provide nearly all of the components need for a network security stack, most customers will maintain a multi-vendor environment for a variety of reasons. This might include, for example, existing installations or business relationships – or the desire to maintain several vendors in best-of-breed relationships or to avoid heavy lock-in to one vendor.
Another consideration is there is a wide variation in enterprise environments and needs. A global energy company would have vastly different needs than a small and medium business or a university, for example. Most organizations will find them in a hybrid environment, managing a variety of end-user devices and security needs, with cybersecurity products that might run on premises or in the cloud. In one recent trend, we have seen SASE vendors adding to their product portfolios to accommodate this hybrid approach.
From a monitoring/visibility perspective, these hybrid and multi-vendor environments will still need cross-platform tools for functions such as orchestration, integration, and network monitoring. With hybrid environments proliferating, the customers will need to consider a holistic, vendor-neutral approach to network monitoring and analysis, to provide full visibility over this complex, heterogeneous estate.
With all of this taken into consideration, we expect the SASE movement to have serious legs. It will also have major benefits. It’s not just the latest fad – it represents a serious effort for managers to integrate and gain control over securing many different types of network connections. . This effort is likely to play out over many years as solutions providers and end users themselves look to integrate network management with a wide range of security functions.
Editor’s Note: AppNeta and Symantec Network Security combine to safeguard user experience as organizations transition to SASE. Learn more.

R. Scott Raynovich
R. Scott Raynovich is the Founder and Chief Analyst of Futuriom, an independent cloud technology analysis firm focused on deep primary research in cloud infrastructure. He has been studying and writing about technology markets as an analyst and writer for 30 years. In the past he was a partner and Editor in Chief of...
Other resources you might be interested in
Automic Automation Cloud Integrations: Google Cloud Run Agent Integration
Broadcom's Google Cloud Run Automation Agent lets you easily execute Google Cloud Run jobs, monitor and manage them with your existing enterprise workload automation, as well as other cloud-native...
Rally Office Hours: February 19, 2026
Learn more about Rally's AI capabilities, including the upcoming MCP server and built-in features, plus follow a Q&A session and upcoming event announcements.
Clarity 101 - From Strategy to Reality
Learn how Clarity helps you achieve Strategic Portfolio Management.
Working with Custom Views in Rally
This course introduces you to working with custom views in Rally.
Rally Office Hours: February 12, 2026
Catch the announcement of the new Rally feature that enables workspace admins to set artifact field ordering. Learn about ongoing research and upcoming events.
The Architecture Shift Powering Network Observability
Discover how NODE (Network Observability Deployment Engine) from Broadcom delivers easier deployment, streamlined upgrades, and enhanced stability.
Rally Office Hours: February 5, 2026
Learn about new endorsed widgets and UX research needs, and hear from the Rally team about key topics like user admin, widget conversion, custom grouping, Slack integration, and Flow State filtering.
AppNeta: Design Browser Workflows for Web App Monitoring
Learn how to design, build, and troubleshoot Selenium-based browser workflows in AppNeta to reliably monitor web applications and validate user experience.
DX NetOps: Time Zone and Business Hours Configuration and Usage
Learn how to set and manage time zones and business hours within DX NetOps Portal to ensure accurate data display and optimize analysis and reporting.